How To Change SSH Port in Linux VPS?
Changing the SSH port number on systems such as Debian, Ubuntu and Cent OS should be considered as an additional security measure to prevent unauthorized access.
When you buy a Linux VPS server, the VPS service provider provides it with the default SSH port 22 or with a dedicated port, so changing the SSH port to a non-standard port increases SSH security to the highest degree.
Here is a brief tutorial on how to change SSH port on Debian, Ubuntu and CentOS.
How to change SSH port number in Linux Server?
Here is a detailed step-by-step guide on how to change the SSH port on all Linux systems in the shortest possible time:
Step 1: Pick a New Port Number
Choose the new port number which is free of use by any other service. Now, let’s take this into our context by using 6065 as the fresh SSH port.
Step 2: Review Ports Status
Try to find out if the given port (6065 in our example) is not occupied by another application that is running.
sudo lsof -i -P -n | grep LISTEN
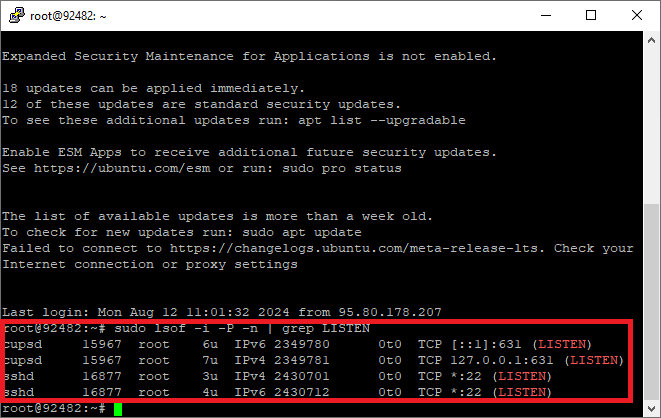
Make sure that the service that uses port 6065 has not already been in use.
Step 3: Open the New Port in the Firewall (iptables)
Set firewall rules to allow incoming SSH connections on new port instead of the old one.
sudo iptables -I INPUT -p tcp --dport 6065 -m conntrack --ctstate NEW,ESTABLISHED -j ACCEPT

This command lets in the traffic of TCP on new port and does this process by the firewall.
Step 4: Change SSH Configuration
Open the SSH server configuration file (sshd_config) and change the SSH port to the new one.
sudo nano /etc/ssh/sshd_config
Find the commented-out line with the SSH port set-up (usually port 22) and change it to read your new port.
Port 6065
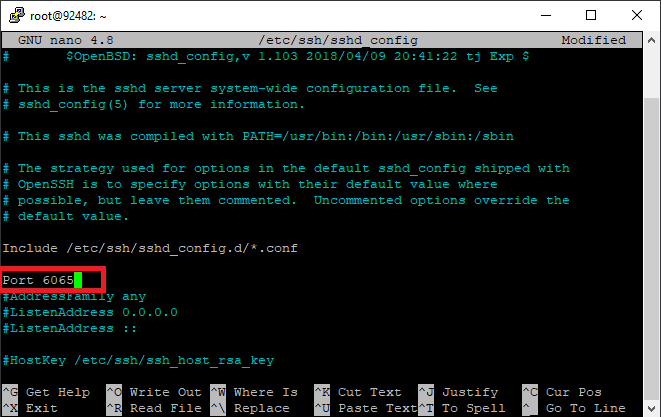
If there is a # symbol at the beginning of the line, delete it. Then, use CTRL + x and enter y to save and exit.
Step 5: Restart SSH Service
Restart the SSH service by issuing the following commands so as to apply the changes made in the configuration file.
sudo systemctl restart sshd
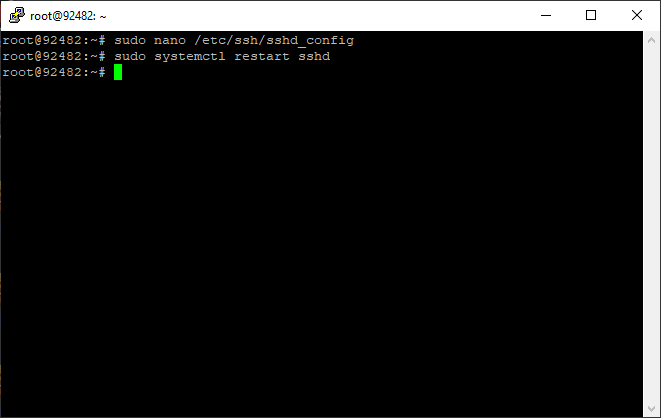
Step 6: Connect through the new port
You can now connect to Linux server through Putty or another ssh connection software using the new port.
This is the easiest way to change the port on Linux server, you can easily change the port of your Linux server for secure connection
What is an SSH Port? (brief explanation)
The SSH port is, therefore, the main port that allows you to connect to a server through the SSH protocol using cryptographic algorithms. Without any manual interference, SSH servers are configured to connect on port 22. It is like the particular address of the server on the Internet: when you want to manage your server by connecting remotely, your SSH client will get the server through this port.
Changing the default SSH port from 22 to another number is often considered an Applicable Security practice. Why? You see, port 22 is very famous, and when these bots try to automatically break into the computers, it is often seen.
A selection of a non-standard port number for the SSH server, such as 2222, for example, should make it more difficult for the automatic scripts to find your SSH server.
Though port redirection isn’t a full solution security-wise, it’s not the be-all and end-all of security. However, it is the fundamental key. Some other important precautions include using passwords such as SSH keys for authentication, configuring the firewall to restrict access, and ensuring periodic software updates.
Normally, the SSH port change adds an additional layer of privacy and requires an attacker to perform more powerful attacks manually. However, port changing is effective only when applied together with other best security practices.
Tips For Changing Linux SSH Port
Changing the SSH port on a Linux system can help enhance security by reducing automated attacks. Here are tips for safely changing the SSH port:
- Choose a four or 5-Digit Port Number: It is advisable during changing SSH port number to use a port number consisting of 4 or 5 digits. g. , 22222 or 55555). This leads to a rather complicated mode and, thereby, the decreasing possibility of carrying on the port scanning attacks.
- Ensure Port Availability: Make sure it is not used for another service, then proceed. By selecting a port number that is rarely used by other protocols, we can avoid conflicts that occur with standard ports.
- Inform Data Center or Network Administrator: When you are in a data center or choose a port that only network administrators who manage firewalls would know about, it could be awkward as they are the only people involved in the process.
- Keep a Record of the New Port: Note down the new port number that will be used further on. Store these data along with other server configurations security-wise.
- Exercise Caution When Making Changes: Modification of SSH port means thereby changing crucial system settings. Be very careful with the configuration file in order to avoid typos or syntax errors since wrong input will certainly lead you to the locked node.
- Consider SELinux: In case you have Security-Enhanced Linux (SELinux) activated on your system, note that any SSH port modifications may require some SELinux policy adjustments as well. If you are unaware of SELinux, think of disabling it to prevent any unintentional problems when your server is underway.
- Update Documentation and Procedures: Once the SSH port has been changed, remember to update any relevant documentation and procedure related to the server access. Let other teams or administrative members know about the port change so that everybody knows the new setup.
You may also use different versions of the Linux server, that’s why we have separately provided the commands for each Linux operating system, CentOS, RHEL, Fedora, Ubuntu, etc.
How to Change SSH Port in CentOS-RHEL-Fedora?
Below is a detailed step-by-step tutorial on how to change the SSH port in CentOS, RHEL (Red Hat Enterprise Linux), or Fedora, including handling SELinux and firewall configurations:
Step 1: Try Checkout SELinux
First, check if SELinux is enabled on your system:
sudo status
If SELinux is enabled, you will see some output stating its status enabling or disabling. In this case, proceed with the following steps. If you think it is disabled, jump to Step 4 or directly proceed to Step 4.
Step 2: Add This New SSH Port to the Strategic Selinux Policy
Use semanage to introduce the new SSH port (e.g., 3333) to SELinux’s list of allowed SSH ports (ssh_port_t):, 3333) to SELinux’s list of allowed SSH ports (ssh_port_t):
sudo semanage port -a -t ssh_port_t -p tcp 3333
This command allows SSH connections on port 3333 through SELinux.
Step 3: Allow the New Port in Firewall (firewall)
Subsequently, enable the firewall to allow incoming SSH port (3333). Assume that you are operating within the public zone:
sudo firewall-cmd --zone=public --add-port=3333/tcp --permanent
This command configures the firewall to open port #3333 to the public domain.
Step 4: Reset the Firewall Filters
Reload the firewall to apply the new configuration changes
sudo firewall-cmd --reload
This command forces the firewall service to reload with the new configuration.
Step 5: Modularize SSH Configuration
Now, go to the SSH server configuration file (sshd_config) to alter it and give the new SSH port as well.
sudo nano /etc/ssh/sshd_config
Find the line that mentions the SSH port (often commented with #Port 22) and change it to use the new port (3333).
Port 3333
Write the changes, press CTRL + O to save, press Enter to confirm, and press CTRL + X to exit the text editor.
Step 6: Install the Keys on the SSH Port
Finally, test the SSH connection using the updated port (3333 in this example):
ssh username@server_ip -p 3333
Additional Tips:
- Make sure that any network firewall or security group restrictions do not limit access.
- Be extremely attentive while modifying configuration files (sshd_config) so as not to introduce any syntactical errors.
- Copy crucial configuration files (sshd_config) once in a while to exit quickly from a file in case of errors after a change.
- Test the SSH connection from a different terminal and client to confirm it is accessible on the new port.
How to Change SSH Port in Ubuntu-Debian-Kali?
Here’s a detailed step-by-step guide on how to change the SSH port in Ubuntu, Debian, or Kali Linux:
Step 1: Select a New Port
Specify a new port number that is not normally associated with other services. Let’s take 2222 as a new SSH port.
Step 2: Open the New Port in UFW (Uncomplicated Firewall)
Allow incoming connections on the new SSH port (2222) using UFW:
ufw allow 2222
This command allows the firewall to accept TCP traffic on a particular port, for example, port 2222.
Step 3: Change The SSH Configuration
Modify the SSH server configuration file (sshd_config) to specify the new SSH port.
sudo nano /etc/ssh/sshd_config
Find the line that indicates the SSH port (Port 22 is already commented out with #Port 22) and edit it to use the new port (2222).
Port 2222
Save the settings and the quit text editor (CTRL + O to write changes, Enter to confirm, CTRL + X to exit).
Step 4: Put Into Trial the New SSH Port
Finally, test the SSH connection using the updated port (2222 in this example):
ssh username@server_ip -p 2222
Use your actual username and server_ip as variations, where the server_ip is either the IP address or the hostname of the server.
Security Measures for Changing SSH Port in Linux (Debian, Ubuntu, Centos)
Here are some additional security measures and tips to further enhance the security of your Linux server:
- Disable Root Login: Instead of going directly into the root of SSH, where the user has root access, the administrator could create a separate user with sudo privilege. To do this, you should disable direct root login in the SSH configuration file (sshd_config).
- Use SSH Keys: Replace authentication with the password system with the SSH key authentication as a second factor. SSH keys could be stronger than passwords, so such problems as brute-force attacks are very unlikely.
- Enable Two-Factor Authentication (2FA): Set up two-factor authentication for SSH logins to add additional protection. In this case, two-factor authentication (i.e. send a phone app code as well) is applied in order to provide an extra layer of protection while users sign in (in addition to their password).
- Regularly Update Software: Maintain the latest security patches for your Linux distribution and software by making sure you update regularly. Install automatic updates wherever possible.
- Use Fail2ban: Set up and configure fail2ban such that it will blacklist unauthorized ip addresses exhibiting abnormal behaviors. For instance, the Fail2ban will automatically blacklist IP addresses trying to log in repeatedly to disrupt the workings of the website.
- Monitor Logs: Build a habit of checking system logs (/var/log/auth. log or /var/log/secure) once in a while for suspicious activities, failed login attempts, or unauthorized access.
- Implement Firewall Rules: You should set the firewall rules (you can use UFW, tables, or other tools) to restrict incoming and outgoing traffic to the necessary ports and IP addresses.
Why is SSH Security Important?
SSH security is crucial for several reasons:
- Remote Access: SSH offers secure remote access to the servers, which helps administrators do system management from anywhere. This convenience comes to the task of securing this access method.
- Protection Against Attacks: Hacking is all about finding and exploiting vulnerabilities. Changing the default port can ensure the anonymity of the server address, making it more difficult for any kind of automatic attack to hit your server.
- Reduced Exposure to Risk: Changing the SSH port protects your server from the standard attack methods by increasing the observers’ efforts. This is a very effective measure that will prevent many automated attacks.
- Preventing Brute Force Attacks: The SSH ports have become a predominant target for brute force attacks. The most viable solution, therefore, would be to reconfigure the port to mitigate these attacks and prevent unauthorized remote access attempts.
- Mitigating Common Threats: Unsecured default ports are prone to increased malware targeting. Altering the default SSH port can decrease common risks and keep your server more secure.
Conclusion
changing the SSH port on Linux systems like Debian, Ubuntu, and CentOS is a good decision for user security since it reduces the exposure of the server to automated attacks launched at the default SSH port (port 22).
The SSH could be setup to listen on an alternate port that is non-standard (ports like 1021 or 8310). In other words, by replacing the “2222” in the address with the star, you add an extra layer of secrecy that can stop unauthorized access attempts.
Nevertheless, you should pair port modification with other security practices such as the use of strong passwords or SSH keys, implementation of firewall rules, and constantly updating system software in order to have a robust security posture.

